Cyber Security Basics
By Steven Castelletto
Comprehensive information from the Cyber Security Basics seminar.
Preventing Data Breaches
There’s a saying when it comes to home security. You don’t need a house that is impossible to break into, you just need to not be the
easiest house on the street to break into. The same rings true when it comes to cyber security. You don’t want to be the low hanging fruit.
Often when people find themselves the target of a scam call or email, they often ask “Why did they pick me?”. The answer is usually the
same: “They didn’t.” Scammers mostly take the throw it at the wall and see what sticks approach. If you find a dodgy email in your inbox,
odds are you’re one of hundreds of thousands of other people to receive the same email. If you receive a call from “the ATO” threatening to
pay an unknown debt or face imprisonment, it’s likely that you’re the hundredth phone number that morning that the scammer has threatened
using the same script and they’re just rolling through each number in the phone book. They know that 99% of their initial attempts will not
be successful. It’s that 1% that they want, and once they have identified that single percent, that’s when the scary stuff starts to happen.
The attack vectors
When it comes to business cyber security, there are usually four key areas in which cyber criminals attempt to stress in order to gain
access to your sensitive information. These pressure points exist through their potential of human error occurring, and it’s like a house of
cards; once one falls, so do the others. Think of it as a house with four doors. You could have the best front door lock, fitted with a
fingerprint scanner and deadbolt, but if you forgot to lock the back door, that front door isn’t going to be doing much good.
These four key areas are:
- Weak and repeated passwords;
- Relaxed physical device security;
- Malware infections due to poor maintenance practices; and
- Social engineering and identity theft.

Good password and authentication practices
Of these four vectors, passwords are the most crucial. These are your front door and the most stressed point from attackers. A study found
that more than 76% of compromised data records were due to poor authentication security. The see what sticks method is the favoured method
by far when it comes to password cracking.
What attackers do here is gain access to a long list of emails they have scraped from all over the internet, go through each one by one and
run password cracking software over it. This software essentially throws hundreds of thousands of password guesses per second at the email
address using common words and names, from “Aardvark1” all the way to” Zythum9999”. If you have a good password, nothing will work, and
they’ll move on to the next email address and you’ll be in the clear. If you’re password isn’t good, odds are you are in for a headache,
especially if you use the same password across other websites, as that email and password will act like a golden key to your other online
accounts and you’ll be at risk to identity theft.
So, what can we do to prevent this from happening?
Firstly, throw out all your single word passwords, even if you have tried to make it more secure by adding symbols to the ends of it, and
replaced some o’s with 0’s and t’s with 7’s. This was a common suggestion over a decade ago that had some merit, but the performance of
computers has increased a hundredfold and the complexity of password cracking software has allowed it to easily account for these variables.
Most experts recommend long passwords consisting of randomised numbers, symbols and letters, however these are extremely difficult to
remember. What you want instead is a long “passphrase” of at least 4-5 words. Passphrases are significantly easier to remember, and just as
secure when long enough. Examples of this can be things like “Favourite-Foods-Pizza-Ice-Cream?“ or “My-Dogs-Name-Is-Rover!”.
Secondly, don’t use repeated passwords. As mentioned previously, sharing the same password amongst all your accounts allows the attacker to
essentially duplicate those login details across websites and gather more information about you as a person and steal your identity.
What you might be thinking now is “how on earth am I going to remember a bunch of unique long random passphrases?”. The answer is, you
don’t. What you want to use is what is known as a password manager. A password manager acts as an online login details list. If you’re the
type of person that has a notebook dedicated to writing down your logins for each website, you know what I’m talking about. The only
difference is that this one can be accessed from a web browser or application wherever you have internet and requires you to enter a master
password to get into it. In addition to storing passwords, these password managers also give you the ability to do the following:
-
Provide automatic password generation - you don’t even need to think of a new password. It can generate an extremely secure password for you
and store it.
-
Autofill password fields – It will detect what website you are using and automatically fill in the email and password field for that
website. The only one password you will need to remember is the master password.
-
Additional tools that warn you if you are using repeated passwords or if any of your passwords have been exposed by a known data breach, and
rate the strength of your passwords.
Finally, another thing you want to be using if the website provides it is two-step authentication (2SA). If a password is your front
security screen door, 2SA is the solid core, deadlocked door behind it. What 2SA essentially does is provide a second verification step to
an account login after successfully entering your password. This verification step needs to be performed from a separate designated device
manually to continue. Basically, even if the attacker knows your account password, there is no possible way for them to gain access without
gaining physical access to your mobile device. Hard to do when you’re likely on another continent!
Bitwarden is an example of password manager software you can use to, well, manage your passwords.
Physical device security
Not all hackers hide behind screens. If you were to ask a hacker what the easiest way is to gain access to a system, they would tell you
getting physical access to the device. There are thousands of different methods to try and get into the information if you have physical
access. Here are a few tips to help you prevent this:
-
The devices that are most at risk are those that can easily be stolen; mobile devices such as smartphones, laptops, and tablets. It is
crucial that these types of devices have passwords and pin codes to prevent access to the system in case of theft. If your device has it,
fingerprint scanners, and 3D facial recognition (i.e. iPhones FaceID) are even better as they add an extra layer on top of the pin code.
-
It’s important that you ensure you aren’t leaving passwords written down around your devices. Use a password manager to store this
information, unless you have a physical safe handy to keep this information behind lock and key.
-
Avoid storing sensitive information on your desktop and remember to regularly clear folders that accumulate files through daily use such as
your Downloads folder and Recycle Bin. These folders are often forgotten about and contain sensitive information you didn’t realise was
still there.
-
Never insert a physical device such as a USB thumb drive into your computer if its origin is unknown. A common technique that hackers use to
install malware onto a computer system is to scatter infected USB thumb drives in public places in the hopes someone curious will pick it up
and see what is on it. Similarly, keep in mind that some malware automatically spreads to external storage devices, so if someone shares a
thumb drive with you, ensure you know their system is not infected or that you have a virus scanner installed on you own to scan the device.
-
Avoid working on shared devices. The family computer is not a great option for working on sensitive files, as you can’t know for sure
whether other users are putting the computer at risk. Kids and computer security do not often mix. If you must use a shared computer, ensure
that each user has their own separate log-ins.
Maintaining your device
Computers are a lot like cars. Learning to check your oil level, cleaning the air filter and knowing the warning signs of a poorly running
car can save you a lot of money and pain later on. Your car is one of those things you sometimes take for granted. You need it to go about
your day to day life without hassle. The same can be said about a computer which you use to manage most of your daily affairs in the digital
era. For something you use so often and are heavily dependant on, it is well worth the effort to invest some time in learning how it works
and how to keep it running as efficiently as possible.
Not knowing how to maintain your computer opens it up to risks of being infected by Malware. What is malware exactly? You probably know it
as a virus, but a virus is just one form of many types of malware. The term malware is a short form of “Malicious Software” and a
generalisation for any type of software designed for the express purpose of acting against the user’s interests. These purposes can range to
something as minor as learning about the user’s browsing history to serve deceitful advertising, to providing a third-party remote access
controls to the device, all the way to entirely holding your precious information at ransom and destroying and corrupting those files.
How can we prevent this?
Set up a weekly process checklist to do the following:
-
Ensure that your computer and software is regularly updated to their latest versions. Software providers often release patches to their
operating systems (I.e. Windows, MacOS, Android, iOS) and programs to fix security vulnerabilities that malware often exploits.
-
Familiarise yourself with your malware/virus scanning software. Run weekly scans and ensure that it is set up to automatically update.
-
Ensure you have a backup solution in place. Even better, use a cloud solution such as Microsoft OneDrive, Google Drive, or Dropbox to house
all your documents and skip this step altogether! Moving to the cloud will ensure that there are always copies of your file saved online,
regardless of what happens to your device. If you have a Microsoft Office subscription, Microsoft OneDrive storage is often included in your
subscription. Another thing worth considering is moving your accounting software to the cloud. No need to backup and manage software updates
yourself. You always have access to a single live file with your accountant via a web browser or app. We highly recommend Xero to all our
clients.
-
Go through your emails and delete any with sensitive information you no longer need when possible. Regularly clean out your deleted items
folders and monitor junk email folder for increased activity.
A final word of warning regarding virus and malware scanners. Having these doesn’t make you immune to infection. Don’t let having one lead
you into a false sense of security. It’s a lot like a flu-shot. It will only protect you from current known strains of the virus. If you
contract a new strain, you’ll get the flu regardless. Malware security is always a game of catch up. Malware is created, machines are
infected, security software vendors work out how to stop it and the software is updated to detect it. There are some exceptions to this rule
with Heuristics which allow malware scanners to detect new malware based on similarities to other malware, but you should never rely on
this. Prevention through careful usage is always better than a cure.
The “Update & Security” section of Settings in Windows 10 allows you to update and protect your computer. Look for the little
gear icon on the left side of the Windows start menu to get to Settings.
Identifying Phishing and protecting your identity online
What is phishing?
Phishing is a form of social engineering where the attacker attempts to imitate another entity in order to manipulate the victim into
handing over personal information or money. These attempts can come in many forms. The email variety usually comes under the guise of a
digital service asking you to confirm an account action by entering in your personal details into a fake website or opening an attachment
that is really malware. The phone variety usually attempts to imitate authoritative entities such as the ATO to coerce via threats to settle
non-existent debts, or tricking you into going to a website to download a remote access tool and malware so they can remove non-existent
(prior to the call) infections.
What can be done to prevent phishing?
Apart from moving to the mountains to live as a hermit in a wooden hut free of technology, nothing can be done to prevent phishing attempts.
It is too easy to obtain emails and phone numbers from the public domain, and too difficult for their relevant systems to block attempts at
phishing. The only thing you can do to protect yourself from these attempts is to learn the warning signs of a phishing attempt and the best
way to respond (or not respond).
What are the warning signs?
-
Phishing calls and emails will often prompt you to take immediate action to induce panic. They attempt to get you to act on impulse rather
than sensibility.
-
There will often be spelling mistakes, bad grammar and poor English in phishing emails. Calls will often contain a robotic message or will
be from someone who is clearly not a native English speaker. A lot of this contact may stem from other parts of the world, often poor
countries with desperate people trying to make money.
-
Phishing attempts may prompt you into opening an attachment, clicking a link, or going to a website to download a program to get you to
install Malware on your device.
-
Phishing emails will often try to mimic the stationery and branding of the entity they are trying to mimic. Check for flaws in the
stationery such as old logos, poor quality, or inconsistent or tacky looking fonts.
-
You will often be addressed generically when receiving this type of contact. Examples of this will be “Dear Sir or Madam” or “Dear Valued
Customer”.
-
The email address may not be from a legitimate email domain. An email domain is the tail of the email address. I.e. @example.com. This
domain should match the website address of that entity. For example, an ATO source email should be from an email domain of @ato.gov.au, not
from @at0.net.
Note that the above warning signs will not be present in all phishing attempts and some legitimate contact attempts may sometimes contain a
warning sign or two. When self-assessing whether contact is legitimate or not, you will need to weigh up whether it is based on all these
signs, not just single ones.
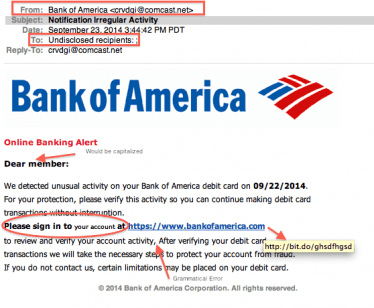
An example of a phishing email trying to impersonate a legitimate banking entity and some tell-tale signs
What else should you do if the warning signs don’t help?
Verify the contact with the party they claim to be separately and trust your gut. If something seems too good to be true, it probably is. If
someone is threatening you or trying to prompt you into immediate action, stop and think. Does this make sense or have any context? Is this
contact out of the blue? Who can I contact to verify the subject of this email or call? Asking yourself these questions and forcing yourself
to think out the situation before acting is often enough to break the spell of confusion and fear these scammers attempt to put you under.
Google is also a powerful resource for working out whether contact is legitimate or not. If receiving a call, try typing in the phone number
from the caller. You may find online reverse number forums where people have reported it as a scam. If an email, try copy and pasting
segments of the email contents into the search box. These emails are usually sent to thousands of people at a time with identical wording.
Often people will post the email on the internet reporting it as a scam.
How else can I protect my identity online?
In this modern world we crave being connected to our friends and family and sharing our lives with them, but life is becoming more and more
busy for people with the efficiency technology brings us. Social media is the solution to this problem. It’s a way to instantly connect with
those we care about. Unfortunately, it’s also a way for identity thieves to instantly gain a snapshot of their victims’ lives.
To a scammer, a social media profile that hasn’t been locked down properly is a gold mine. From that profile they can get everything they
need to effectively impersonate a person and use that to gain access to stuff they previously would not have been able to. Ever set a secret
question to an online account to be the usual default “What is your mother’s maiden name?”. If so, that could easily be worked out via a
social media profile.
So, what can you do to prevent this? For each social network you are on, it is important to review your privacy settings. Through these
settings so you can control exactly who you share your profile and its content with.

Facebook privacy settings
Another way to protect your information online is to utilise Virtual Private Networks (VPN). VPNs encrypt all your data in transit.
Understanding what this means requires a little knowledge of how your data gets from point A to point B on the Internet. The short version
is that your data travels along several different jump points (web servers) to get to its final destination which is the website you
interact with. If one of those web servers is compromised by someone (whether that be a cyber-criminal, or someone engaging in espionage) it
is possible, if your data is not encrypted, for that party to access your sensitive information during transit. Think of it as an
international flight with the stopover being in a fairly sketchy country where there have been cases of luggage theft during the stopover.
What a VPN does is reroute your data to a specific trusted server first, where it is encrypted making it unreadable without a specific key
that only the VPN servers have, then push it to another server which is owned by the VPN host that decrypts the data, so your final
destination website can read it. Using the international flight example, it basically allows you to choose your stopover to be a trusted
airport, locks up your luggage when they land in that stopover and stays locked until you reach your final arrival location.
One final note regarding VPNs. Ensure that the VPN host is a reputable one that you can trust. Free VPN’s are a no go as they usually have
poor performance and may be sketchy themselves. Look for VPN providers that are transparent and advocates of privacy on the Internet.
Summary and final word.
- Create strong and unique passwords or passphrases.
- Leverage password managers to keep track of and create secure passwords and passphrases.
- Use two-factor authentication.
- Keep your physical devices locked down and secure.
- Never opt for convenience over security.
- Familiarise yourself with basic computer maintenance tasks to protect from malware.
- Regularly perform backups, or leverage the cloud to do the work for you.
- Avoid working on shared devices.
- Recognise the warning signs of phishing and trust your gut.
- Lock down social media profiles.
-
Look into VPNs if your data is especially sensitive and travels over the Internet. Ensure you do your research into finding the most trusted
VPN host.
One more piece of advice. Establish a professional relationship with an IT professional so that you have someone to quickly turn to if you
ever have a computer security issue. If you are a business with high reliance on your data and systems, this is even more crucial. Set up
comprehensive action plans with steps you would take to mitigate damage from a data breach and set up systems in place to prevent it. Do not
overlook your IT processes because they appear to be working fine currently. All it takes is one wrong click and suddenly your business
can’t operate effectively, and you are in a scramble trying to work out what to do next. IT processes should be regularly reviewed and
updated alongside your business and bookkeeping processes.
Steven Castelletto
Accountant








